LabVIEW Hill Cipher Encryption
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report to a Moderator
Products and Environment
This section reflects the products and operating system used to create the example.To download NI software, including the products shown below, visit ni.com/downloads.
- LabVIEW
Software
Code and Documents
Attachment
Overview
This example shows how to encrypt a string of data using the simple Hill cipher.
Description
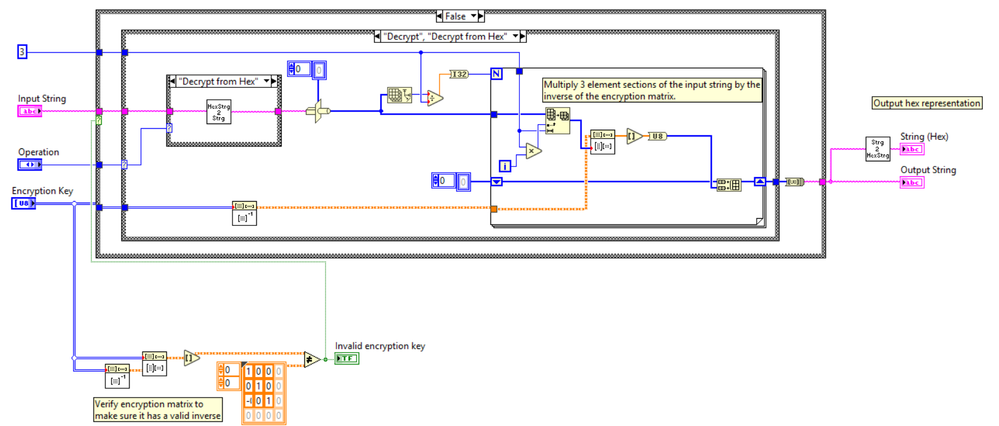
This example shows how to encrypt a string of data using the simple Hill cipher. It is not a very strong encryption scheme but will suffice for many basic applications. The VI can encrypt and decrypt a string. Because the encrypted string can contain characters which may be difficult to transfer over a network or store in a file, the VI also generates a hexadecimal version of the string which can be easily shared. For decryption you can choose to use the original string or the hexadecimal version of the string.
The chosen encryption key must be a matrix with a valid inverse. The VI checks for the validity of the encryption key. In the example the encryption key is a 3x3 matrix, but the example can be easily expanded to use larger square matrices.
Requirements
LabVIEW Full Development System 2012 or compatible
Steps to Implement or Execute Code
- Enter the string to be encrypted in Input String
- Select the requested Operation (Encrypt, Decrypt, Decrypt from Hex)
- Enter the Encryption Key matrix
- Run the VI
- The VI will calculate the Output String and String (Hex)
Additional Information or References
Information on the Hill cipher can be found in Wikipedia here.
VI Block Diagram
**This document has been updated to meet the current required format for the NI Code Exchange. **
Example code from the Example Code Exchange in the NI Community is licensed with the MIT license.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
The adding of Null characters creates blank spaces at end of string, which makes the result string when encrypted and decrypted not equal to the original string.